Two-Factor Authentication for WordPress
How to secure user accounts and prevent account takeover with two-factor authentication
Two-Factor Authentication or 2FA provides an additional layer of security requiring a second factor of identification beyond just a username and password. Two-factor authentication has long been used to control access to personal and financial data processed in banks or insurance companies; and today website owners are increasingly using 2FA to protect their users’ accounts from cybercriminals exploiting weak or stolen WordPress passwords and compromised credentials.
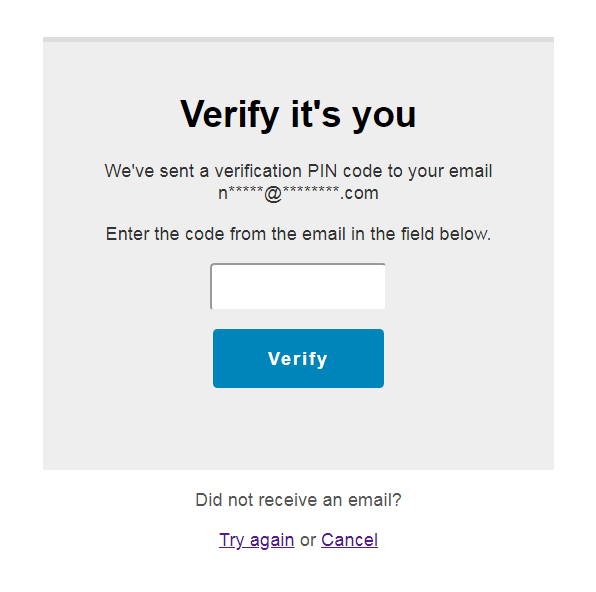
When 2FA is enabled on a website, it requires a user to provide an additional verification PIN code when signing into the website. This verification code is generated automatically and sent to the user by email. As an additional security measure, you can specify a separate email address on a per-user basis specifically for delivering 2FA verification codes.
To continue the user has to enter the verification PIN code into the form. If the user didn’t receive the code, they can either try to get another one or cancel the login process.
How to enable Two-Factor Authentication
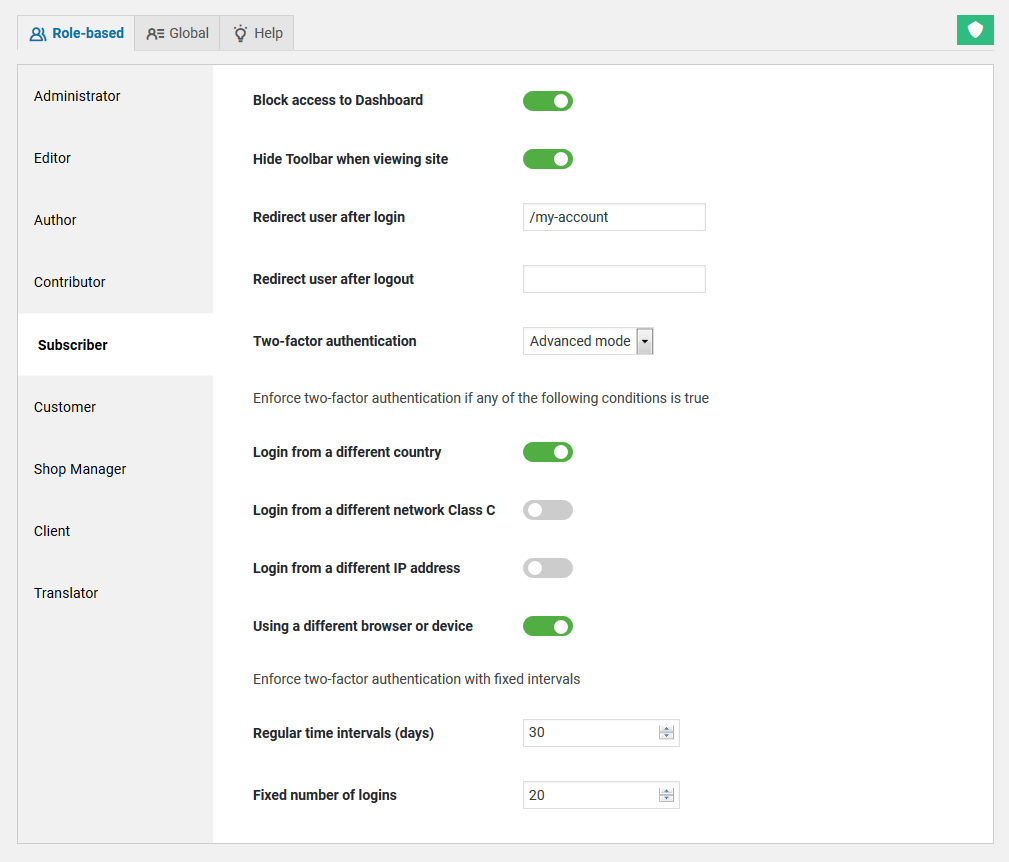
You can easily enable 2FA on a per-role basis on the User Policies admin page. WP Cerber Security enables you to configure different 2FA settings for each role. In the Advanced mode, you can specify a set of conditions for enforcing two-factor authentication for a certain role. The Advanced mode is available in the Professional version of the plugin.
Note: Before you can enable 2FA for administrators’ accounts, you have to complete one successful login with 2FA enabled for any other role on the website.
Per-user 2FA settings
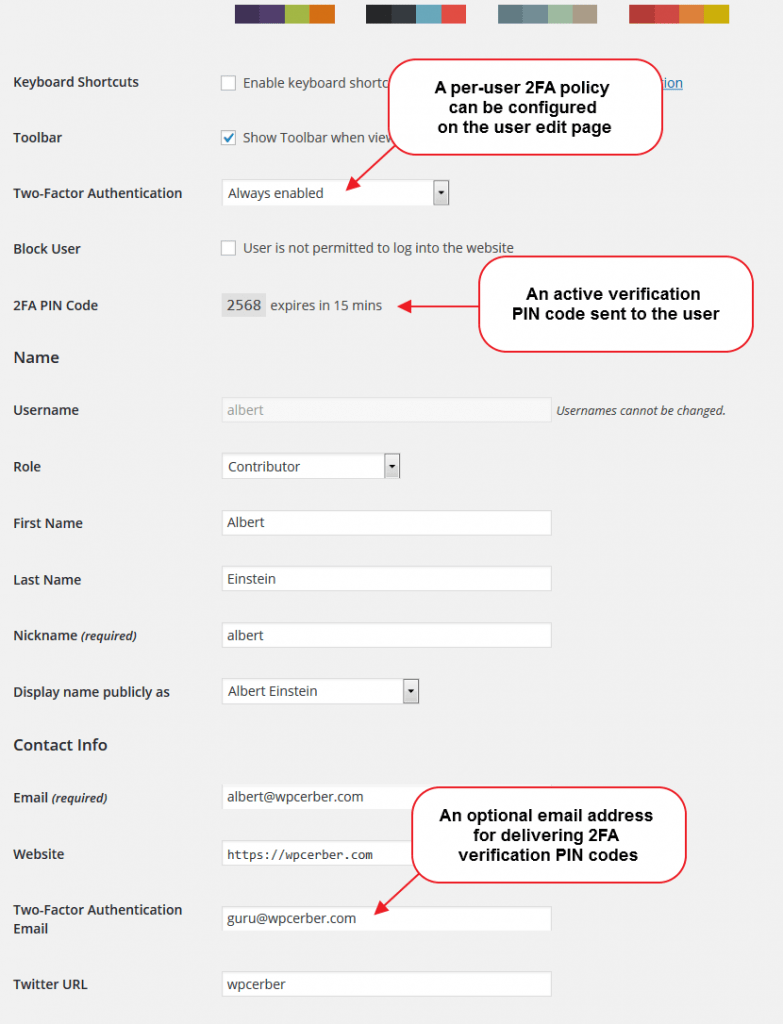
You can customize some 2FA settings on a per-user basis on the user edit page (user profile page). Additionally to per-role 2FA settings, you can disable or enable two-factor authentication for a specific user. You can choose from “Always enabled”, “Disabled” and “Determined by user role policies”. This feature is available in the professional version of WP Cerber.
As an additional security measure, you can specify a separate email address specifically for delivering verification codes.
Whitelisting IP addresses
All WordPress users that are logging in from IP addresses in the White IP Access List are excluded from being enforced two-factor authentication.
Monitoring two-factor authentication events
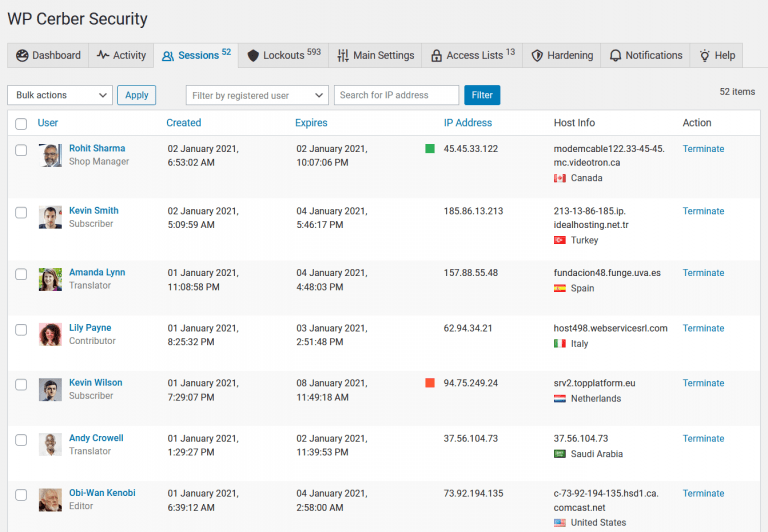
When two-factor authentication is enforced for a user, WP Cerber logs this event to the Activity log as “Two-factor authentication enforced”. At this moment a new verification PIN code is generated and sent ot the user. When a user enters the correct verification PIN code the login event is marked as “2FA code verified”.
To monitor user logins made with two-factor authentication, go to the Activity log, select “Two-factor authentication enforced” event from the drop-down list and click the Filter button.
How to manage 2FA settings on multiple websites
Do you know that you can monitor and manage 2FA settings on any number of websites remotely? Enable a Cerber.Hub remote management technology to manage all WP Cerber settings and monitor user activity from one WordPress dashboard.
Note that some 2FA features are available in the professional version only.
| Features | Free | Professional |
| Standard 2FA mode | Yes | Yes |
| Advanced 2FA mode | No | Yes |
| Per-user 2FA policies | No | Yes |
| Separate email address for 2FA codes | No | Yes |
| Managing 2FA on multiple websites | No | Yes |
Have any questions?
If you have a question regarding WordPress security or WP Cerber, ask it in the comments below or find answers on the community forum.
Spotted a bug or glitch?
We’d love to fix it! Share your bug discoveries with us here: Bug Report.




Updated to v8.3 and I see two factor in the user policies. However, the field says disabled and it is grayed out so I can’t edit it. If this feature only available in the professional version or am I doing something wrong?
Yes, you’re right, the advanced 2FA mode is available in the professional version only. In the free version, the standard 2FA mode is available.
I love this plugin – but why email the code for 2FA?
Why not use an app like Google Authenticator or something like Bitwarden’s built in OTP options.
That’s a good question. We have many reasons. Primarily because email is one of the most reliable channels on this planet for delivering 2FA codes.
I don’t understand what I’m able to do with standard 2FA mode.
I’m using the free version of Cerber plugin, and I don’t see any possibility to enable 2FA.
I enabled it for editors, then logged in with an editor’s account and no second factor was required. Also, I still can’t enable 2FA for the admin role.
If role-based 2FA is available only for Pro version, then what is the kind of 2FA I can enable with the free version?
Please make sure that your IP address is not in the white IP access list. Standard role-based 2FA is available in the free version, the advanced 2FA requires the pro version.
Can you please answer why the “Two-factor authentication” setting for Administrators is un-clickable/non-configurable in the free version of Cerber?
This is weird and confusing because this option it’s working for all other user roles, but not for administrators. I only want to enable 2FA for administrators and right now I can’t do that. I want to choose the “Always enabled” option, not the “Advanced mode”, so it should be available in the free version, right? Is this a bug and if so can you fix it?
Before you can enable 2FA for the administrator role, you have to complete one successful login with 2FA enabled for any other role on the website.
Why did you choose this approach? I’ll mean in most cases there is only one account for a WordPress instance… and administrators should be the most secure account. Now in my case, I’ll need to make a different account just for this purpose and then remove it again. Would be better if you make a change to this that administrators could do this by default and maybe work with backup codes for lockouts.
We had a reason to implement it this way. In one of the next releases, it will be implemented in a more convenient way, without involving other accounts.
No OTP (or U2F) support “[p]rimarily because email is one of the most reliable channels on this planet for delivering 2FA codes”? Is that the legitimate justification for the lack-of this practically-required-in-any-secure-infrastructure feature?
Going with that logic: A compromised email account, one that let’s say *doesn’t* have MFA enabled on it (because the User read somewhere on a security blog that it was ‘the most reliable’) would then be the ultimate keys-to-the-kingdom for this security plugin? Am I understanding that correctly? *Especially* when you combine plugging-in the Cloudflare Global API Key with the add-on; I just checked and your the Cloudflare GLOBAL API key is totally exposed in the clear to the User and in the database!
Stumbling upon that comment from nearly a year ago legitimately makes me re-think my on-going subscription.
Yikes.
When it comes to WordPress, email is one of the best channels. Why? Because you should consider ALL aspects and advantages of using email in the context of 2FA for WordPress. Email is free, it’s easy to manage, it’s a native part of customer mobile devices and WordPress itself, it has no issues with privacy or GDPR, users don’t have to buy, install and manage a mobile application, you can receive 2FA pins on any device, and most importantly, it’s secure because unlike text/SMS messages, no apps or viruses on a mobile device have access to emails. Can an email account be compromised? It’s not an argument because any channel can be compromised.
Cloudflare API key is not exposed anywhere except the Cloudflare add-on admin page. Only the website admin has access to the Cloudflare API key. And yes, it is saved as is in an unencrypted way because Cloudflare servers accept API keys in an unencrypted form.
Greg, I have verified that the Cloudflare Global API Key is in the clear within the database. under the default WordPress Options Table. This is like a password, it should be hashed and obscured as much as possible. If I can go from email to admin login and dump the database, the connected Cloudflare account becomes entirely exposed. L
I suggest this CloudFlare article where they describe the criticality of this themselves. You.must protect this key by all means necessary.
https://blog.cloudflare.com/keeping-our-users-safe/
All API keys have to be stored in an unencrypted form because it’s their nature. Please, post Cloudflare-related questions on this page: https://wpcerber.com/cloudflare-add-on-wp-cerber/
Are you guys planning to implement 2FA over SMS?
It will be implemented using a mobile authenticator app. SMS is not secure enough and, in many countries, it’s not always easy to set up. Anyway, stay tuned.