WP Cerber Security 8.8.3
New login security features
Disabling the default WordPress user authentication through the wp-login.php and using it as a honeypot
When enabled, WP Cerber prevents any user authentication even with correct usernames and passwords. After an attempt to log in, WP Cerber shows the default incorrect password error message mimicking the standard authentication process. Now WP Cerber uses wp-login.php as a detection honeypot for slow brute-force attacks. In the plugin logs, such events are logged as “Attempt to log in denied. Forbidden URL”. This feature replaces and extends the old feature “Block direct access to wp-login.php and return HTTP 404 Not Found Error”. Know more.
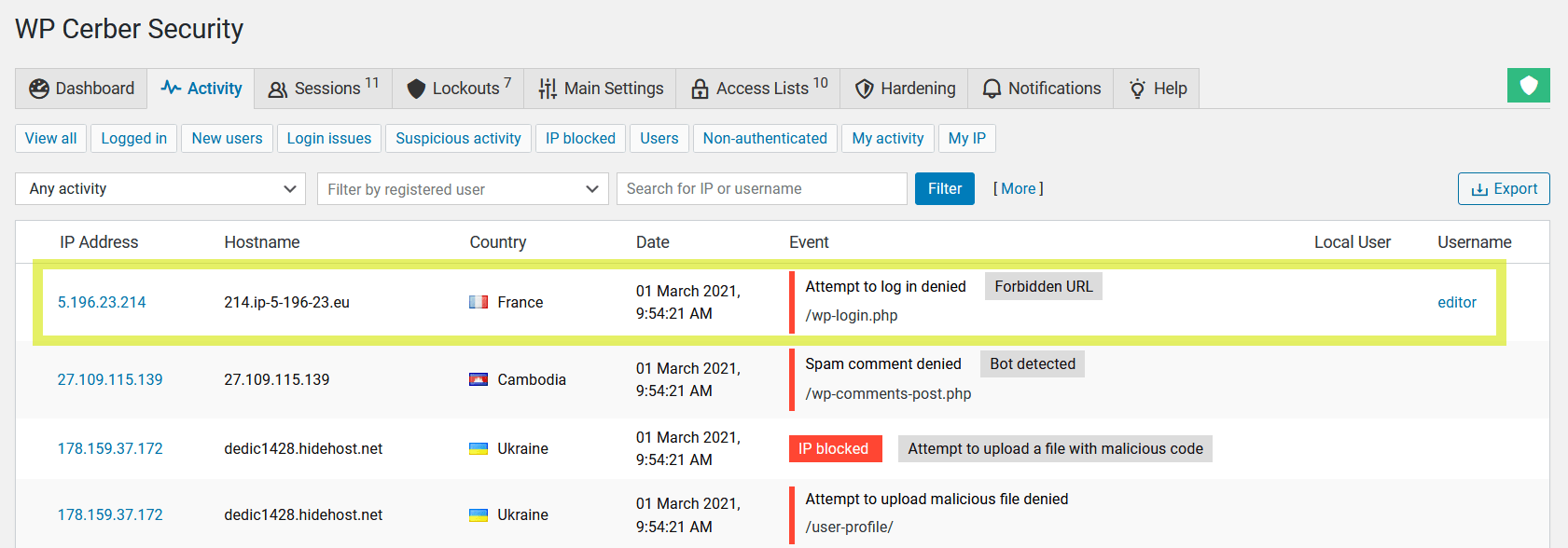
WP Cerber denies attempts to log in via wp-login.php and logs such events with the Forbidden URL label.
Disabling WordPress login hints in the login error message
When enabled, the login error message does not indicate invalid usernames and emails when attempting to log in with non-existing ones. This helps to prevent bad actors from guessing valid usernames.
Disabling WordPress hints in the password reset error message
When enabled, the password reset error message does not indicate invalid usernames and emails when attempting to reset passwords for non-existing accounts. This helps to prevent bad actors from guessing valid usernames. Requires WordPress 5.5. or newer.
Prevent hackers from discovering usernames
New features prevent bad actors from discovering usernames by using oEmbed protocol and via user XML sitemaps introduced in WordPress 5.5. The new settings are located on the Hardening tab.
Multiple improvements to the WP Cerber admin pages
- Update to WP Cerber’s main dashboard page. User and malicious activity are displayed separately in two different areas.
- More convenient navigation through the WP Cerber admin pages by having the admin menu at the top. When you open any WP Cerber admin page, the WP Cerber admin menu will be shown at the top of the WordPress admin sidebar menu. When you navigate away, the menu will be rendered at the default position. The new setting is on the Main Settings admin page.
- A new quick link “Login issues” on the dashboard to view all login issues such as failed logins, denied attempts, attempts to reset passwords, and so forth.
Miscellaneous improvements and optimizations
- Reduced the number of false positives when the malware scanner inspecting directives with external IP addresses in .htaccess files.
- The size of the database tables used by the integrity checker and malware scanner has been reduced.
- Better Two-factor authentication (2FA) emails: the wording of the verification email has been updated and now can be translated. The email subject includes the site name.
- Implemented a strictly secure way of utilizing the unserialize() PHP function known for being used to deliver and run malicious code. It is active on PHP 7.0 and newer.
- Implemented a backup way of running WP Cerber maintenance tasks if WordPress scheduled tasks are not configured properly or failed to get launched.
- Several WP Cerber PHP files have been renamed. You will see several orphaned files in the plugin folder. They have to be safely deleted during the plugin integrity scan on the scanner page. The scanner shows them as “Unattended suspicious file.”
Bug fixes
- Fixed bug: Two-factor authentication (2FA) PINs are not displayed on the edit user admin pages in the WordPress dashboard.
- Fixed bug: The “API request authorization failed” event was logged as “Login failed.”
Wonder what WP Cerber got in the previous version?
Review the release note for WP Cerber Security 8.8.
How to update WP Cerber
We recommend enabling automatic updates to ensure you always have the latest security features and performance improvements: how to enable automatic updates in the plugin settings.
How to install WP Cerber
New to WP Cerber? Follow this step-by-step guide to install WP Cerber on your WordPress.
Have any questions?
If you have a question regarding WordPress security or WP Cerber, ask it in the comments below or find answers on the community forum.
Spotted a bug or glitch?
We’d love to fix it! Share your bug discoveries with us here: Bug Report.