Strong login security with WP Cerber
It’s no secret that bad actors can break into a newly installed WordPress within a few minutes by mounting a brute-force attack. It’s possible because WordPress has no built-in attack mitigation mechanisms, the default login URL is well known, and the username of a website’s admin can be discovered with ease. WP Cerber brings all the necessary tools to mitigate brute-force attacks and safeguard user accounts.
Configuring WP Cerber’s login security settings
The login security settings are located on the Main Settings tab. Here you can configure the limits on login attempts, restrict access to wp-login.php, and configure error messages to prevent discovering usernames and emails when using non-existing usernames and emails.
Limiting login attempts to mitigate brute-force attacks
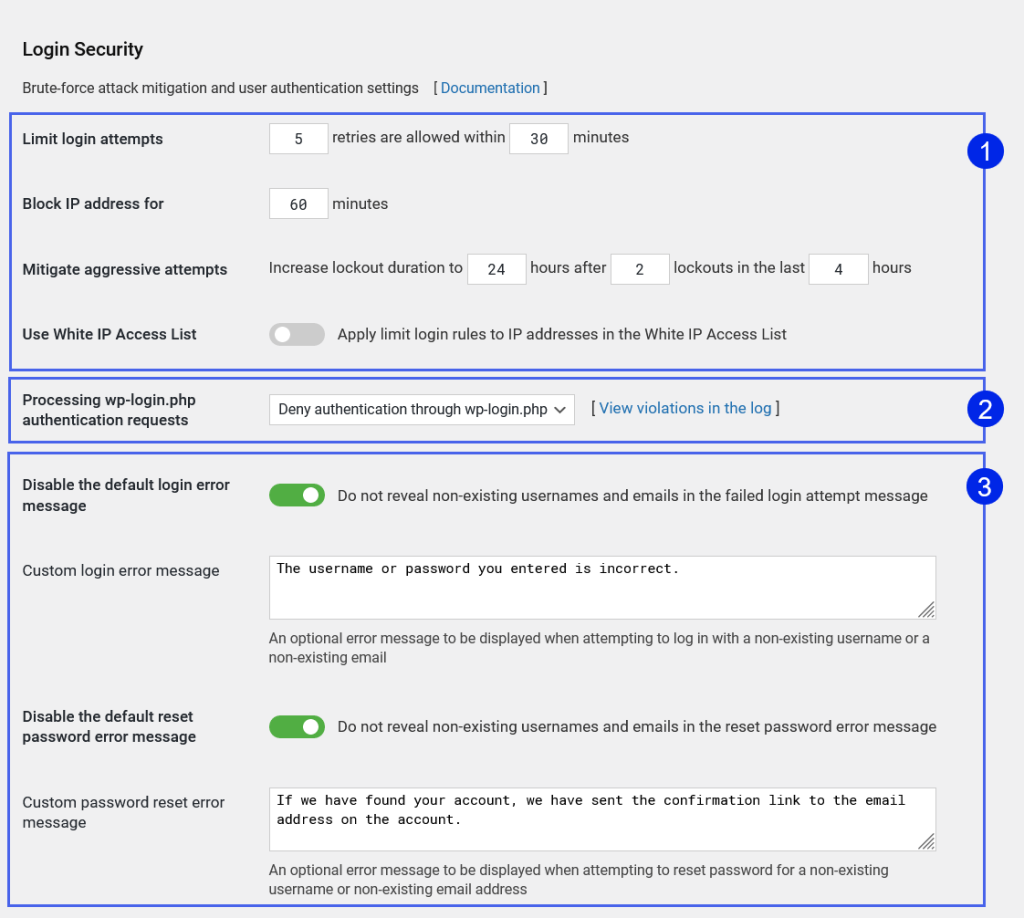
The default and recommended settings for limiting login attempts are highlighted as #1 on the screenshot. These settings were set when you activated WP Cerber. If you have many customers on the website, for instance, you run a WooCommerce store, it makes sense to increase the limit on login attempts.
Processing wp-login.php authentication requests
See selection #2. By default, WordPress uses wp-login.php as the website login page that processes all user logins as well as provides the registration form and the password reset form. If you have configured the Custom login URL, it is recommended to disable wp-login.php. You have two options. You can completely block access to wp-login.php and make the file inaccessible for anyone, or you can disable user authentication through wp-login.php without blocking access to the file. You can choose any of the options. Both prevent user authentication via wp-login.php.
When the first option is enabled, WP Cerber renders and returns the “404 Page Not Found” error page like there is no such file on the website. Thus, bad actors have nothing to attack.
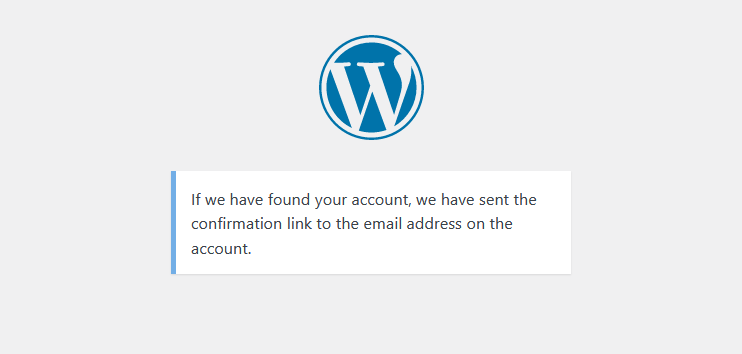
When the second option is enabled, WP Cerber prevents any user authentication even with correct usernames and passwords. This means nobody is able to log in using wp-login.php. After an attempt to log in via wp-login.php, WP Cerber shows the default incorrect password error message mimicking the standard WordPress authentication process. Using this approach helps WP Cerber to detect slow brute-force attacks by using wp-login.php as a detection honeypot. All attempts to log in via wp-login.php are logged to the WP Cerber activity log, as shown on the screenshot below.
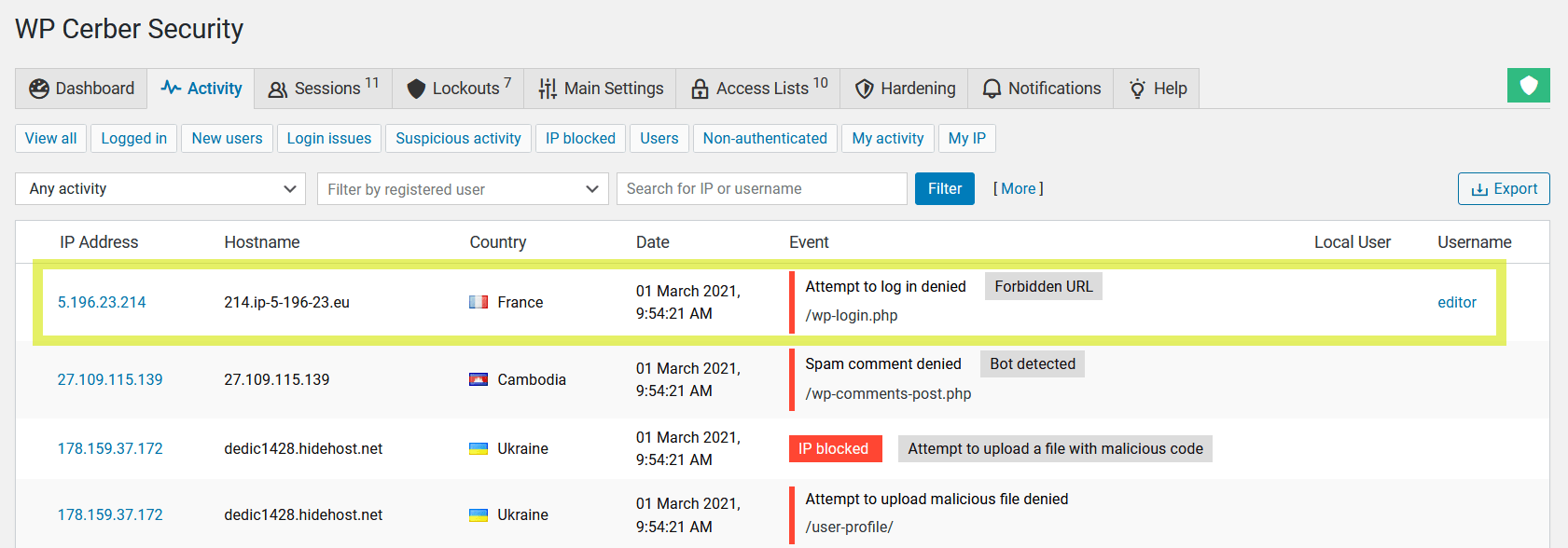
WP Cerber denies attempts to log in via wp-login.php and logs such events with the Forbidden URL label
Prevent bad actors from discovering real usernames and customers’ emails
The default login and password reset error messages generated by WordPress are quite verbose and help hackers detect real usernames and emails to use them for mounting brute-force or social engineering attacks.
Disable the default login error message
When enabled, the login error messages do not indicate invalid usernames and emails when attempting to log in with non-existing ones. Instead, WP Cerber displays the default WordPress error message used when a user enters an incorrect password. This helps prevent bad actors from guessing valid usernames and emails. This approach is also known as disabling login hints.
The professional version of WP Cerber enables you to specify your own login error message using the Custom login error message setting field.
Disable the default reset password error message
When enabled, the password reset error messages do not indicate invalid usernames and emails when attempting to reset the password for a non-existing username or a non-existing email. Instead, WP Cerber mimics the default process of resetting passwords and displays the following message whenever users enter valid or non-existing usernames and emails.
This approach helps prevent bad actors from guessing valid usernames and is known as disabling password reset hints.
The professional version of WP Cerber enables you to specify your own password reset error message using the Custom login error message setting field.
Note that all features described above do not apply to the IP addresses in the White IP Access List.
Have any questions?
If you have a question regarding WordPress security or WP Cerber, ask it in the comments below or find answers on the community forum.
Spotted a bug or glitch?
We’d love to fix it! Share your bug discoveries with us here: Bug Report.