Restrict access to the WordPress REST API
It's time to take control of WordPress REST API
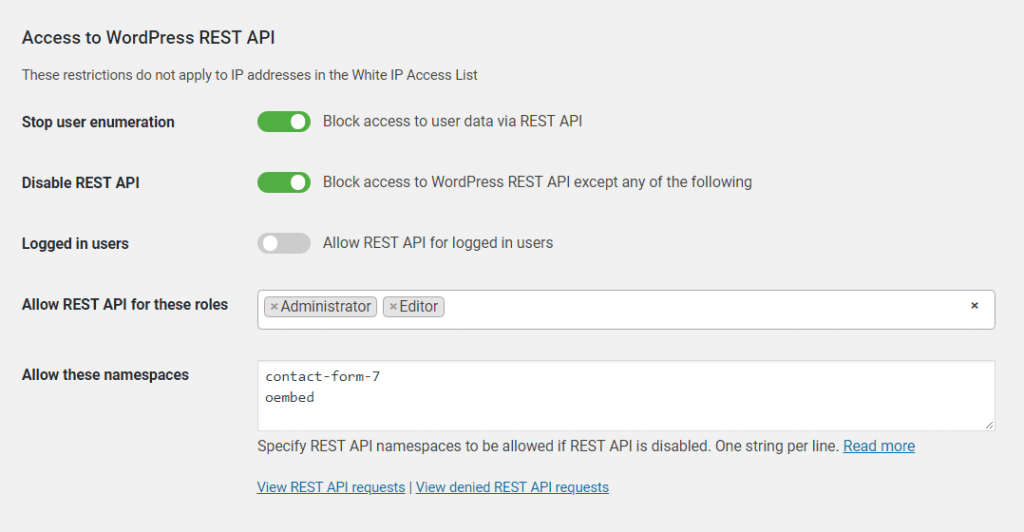
WP Cerber Security allows you to restrict or completely block access to WordPress REST API which is enabled by default. To enable protection go to the Hardening tab and enable Block access to WordPress REST API except any of the following. This blocks access to the REST API unless you grant access to it in the settings fields below or add an IP to the White IP Access List.
If you use Contact Form 7, Jetpack or another plugin that makes use of REST API, you need to whitelist its REST API namespaces as described below.
Permit access to a specific REST API namespace
A REST API namespace is a part of a request URL that allows WordPress to recognize what program code processes a certain REST API request. To get the namespace, take a string between /wp-json/ and the next slash in the REST URL. Note that every plugin that utilizes REST API uses its own unique namespace. The table below shows the namespaces of some plugins.
| Plugin | Namespace |
| Contact Form 7 | contact-form-7 |
| Caldera Forms | cf-api |
| Yoast SEO | yoast |
| Jetpack | jetpack |
| Gravity Forms | gf |
Specify namespace exceptions for REST API if it’s needed as shown on the screenshot
Permit your users to use REST API
Enable Allow REST API for logged in users if you want to allow using REST API for any authorized (logged in) WordPress user without limitation.
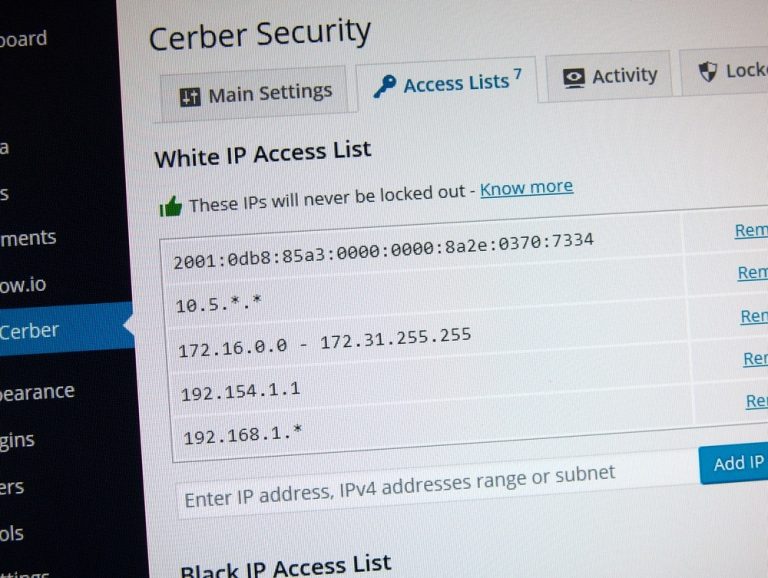
Restrict access to WordPress REST API by IP addresses
To permit access to REST API from a specific IP address or an IP network add them to the White IP Access List.
To completely block access to REST API from a specific IP address or an IP network add them to the Black IP Access List.
Read more: Using IP Access Lists to protect WordPress
How to stop REST API user enumeration
To block access to users’ data and to stop user enumeration via REST API you need to enable the Block access to users’ data via REST API setting on the Hardening tab. This security feature is designed to detect and prevent hackers from scanning your site for user logins and sensitive users’ data.
When it’s enabled Cerber blocks all request to REST API and return HTTP 403 Error. You can monitor such events on the Activity tab. They are logged as “Request to REST API denied”.
Access to users’ data via WordPress REST API is always granted in two cases:
- For administrator accounts, meaning if “Stop user enumeration” via REST API is enabled, all users with the administrator role always have access to users’ data
- For all IP addresses in the White IP Access List
What is REST API?
In a nutshell, it’s a technology that allows two different pieces of code (applications) to talk to each other and exchange data in a standardized way. Using REST API enables developers to create, read and update WordPress content from external applications running on a remote computer or a website. The WP REST API is enabled by default starting the WordPress version 4.7.0.
Read more: Why it’s important to restrict access to the WP REST API
Developers documentation: https://developer.wordpress.org/rest-api/
Do you know that you can manage REST API settings on any number of websites remotely? Enable a main website mode on the main Cerber.Hub website and a managed website mode on your other websites to manage all WP Cerber instances from one dashboard.
Next steps that’ll strengthen your WordPress security
- How to block spam user registrations
- How to block spam form submissions
- How to block a WordPress user
- How to block access from a specific IP address
- How to disable using a specific username
What’s the Cerber Security, anyway? It’s a complete security solution for WordPress which is evolved from a simple yet effective limit login attempts plugin.
Have any questions?
If you have a question regarding WordPress security or WP Cerber, ask it in the comments below or find answers on the community forum.
Spotted a bug or glitch?
We’d love to fix it! Share your bug discoveries with us here: Bug Report.


OK. But how do I know whether a plugin uses the REST API so I have to add it to the namespace access-list?
1. From the documentation on a plugin.
2. Checking for REST API requests on the Live Traffic page: just click the small “REST API” button above the table.
3. If you know the REST API namespace that is used by a plugin you can search for requests by entering that REST API namespace on the Advanced search form in the “URL contains” field.
4. Disable REST API in the settings completely and check how the plugin works. If the plugin doesn’t work anymore, that means it uses REST API. To find out its namespace look for “Request to REST API denied” events the Activity page.
Mmm… thnx, but that does not really make me happy. I checked e.g. the contact form and that worked because the REST API works for the administrator. For me small blogger with 22 plugins operational this becomes a nuisance and a lot of time and work. Can’t this be done automatically eg by suggesting or something?
And while we are talking, why should I not permit /oembed/ as a permitted namespace? It seems to be used by a robot (and of course Cerber blocks it correctly 🙂 ).
For other questions I will use the support blog as I normally do.
Sorry for the kind of abuse of this blog. Won’t do it again.
Just found out that the Gutenberg plugin, the current and default editor is also prevented from working if the rest-api is blocked for logged-in users.
Is there a way to allow this by default?
By default, Cerber doesn’t block REST API for logged-in users since version 7.5. If you installed the plugin earlier this version, you need to manually enable “Allow REST API for logged in users”.
I was receiving a lot of request denied plugin “Redirection”
/wp-json/redirection/v1/group/?_wpnonce=werfsdghdfgdf5
After reading the article I understood how it works I include the REST API namespace “redirection” and is now working. But it took me a while to find the solution.
Trying to apply this on custom post types. While it works for posts, it’s not working for a custom post type. Any suggestions? Thank you!
What are you trying to achieve? Generally speaking, this feature has nothing to do with any post type.
This feature allowed me to restrict access to posts and pages, but the custom post type directories did not get blocked. So when I browse to the json directory of any post or page it shows me the restricted access message, but when I do so for a custom post type, it doesn’t block it.
Example:
https://mywebsite.com/wp-json/wp/v2/posts –> gives a restricted access message.
https://mywebsite.com/wp-json/wp/v2/books –> populates the json file for books.
https://mywebsite.com/wp-json/wp/v2/randomstuff –> where randomstuff = literally any random word: blocks it for me.
For context, I use pods to create the custom post types, although that’s most probably irrelevant.
Please make sure that your IP address is not in the White IP Access List. You can enable the Smart mode for traffic logging, then open that REST API for books in your browser and then check the Live Traffic log for requests from your IP address.
Hello Cerber,
ive been trying this plugin and it works like charm. Only recently i noticed the rest API part didn’t work as I expected. i turned the “disable rest API” and leave the roles and namespace blank and call the rest api using curl, eg
curl “https://example.com/wc/v3/orders -u :”
and it still outputting all orders from my woocommerce store. am i blocking my rest ap in the cerber setting wrong?
The URL in your example has nothing to do with WordPress REST API because it doesn’t start with “wp-json”. A valid REST API URL looks like this one: https://wpcerber.com/wp-json/wp/v2/posts
i mistyped the command
curl “https://example.com/wp-json/wc/v3/orders -u key:secret”
this command works and it outputs all my orders in my store even though i blocked REST API with no exclusion
Is your WordPress installed in a subfolder?
Please install the latest version of WP Cerber. It will work normally in your case.
I did that. It’s already blocking posts and pages on my IP address so it’s not an IP address issue. Seems more like an inability of the plugin to detect CPTs.
No, the plugin handles REST API requests to custom post types perfectly with no issues. You can try those examples: https://developer.wordpress.org/rest-api/extending-the-rest-api/adding-rest-api-support-for-custom-content-types/
Thank you Gregory.
Again, the Rest API is working and is all set up!! But while the pages and posts are blocked and not everyone can access them, books are not and are open to everyone.
The link really doesn’t help. Appreciate it though.
Is your WordPress installed in a subfolder?
Hello Gregory, thank you for your help.
I believe it is, I am using flywheel as a host and I think that’s how they set it up. What do you recommend?
Thank you.
Please install the latest version of WP Cerber. It will work normally in your case.
Hi there, I posted the following on g2.com too, but didn’t get any response:
I’m trying to allow programmatical access to some custom post types via the WP REST API.
when trying to access the API like this:
curl –user “%USERNAME%$APPLICATION PASSWORD%” https://MY.WEBSITE.COM/wp-json/wp/v2/radar-tracker-law
the traffic inspector shows:
/wp-json/wp/v2/radar-tracker-law
Get REST API HTTP 403 Forbidden
I read the instructions (i.e.: https://wpcerber.com/restrict-access-to-wordpress-rest-api/) and have accumulated the following entries in the ‘Allow these namespaces’ settings page:
oembed
legals_text
radar-tracker-law
v2
v2/radar-tracker-law
But I always get:
403 Access Forbidden
Your request looks suspiciously similar to automated requests from spam posting software or it has been denied by a security policy configured by the website administrator.
I also disabled the traffic inspection and set the Anti-Spam engine to ‘Safe mode’ and also added these strings to the whitelist section of the Anti-Spam engine:
radar-tracker-law
wp
v2
/wp-json/wp/v2/radar-tracker-law
Trying from a whitelisted IP address works just fine.
Disabling the Cerber plugin also ‘fixes’ my problem.
Does anybody see what I am doing wrong?
In your case, since it’s REST API, you need to add the namespace “wp” to the “Allow these namespaces” list, which is on the Hardening tab. That’s it.
If I add namespaces to the “Allow these namespaces”, does that allow those entries for ALL users including anonymous or, only for the roles specified?
For all users including anonymous. It’s an “OR logic” for the three settings below the “Block access to WordPress REST API except any of the following” checkbox.