WP Cerber Security 9.6.4
We continue enhancing the stability and performance of WP Cerber while refactoring its legacy code. As we adopt the latest software technologies available in modern web servers and PHP versions, WP Cerber remains compatible with PHP 7.0. However, we strongly recommend using PHP 7.4 or newer. The same applies to WordPress, where we advise upgrading to the latest version for optimal security and performance. Each WordPress release addresses critical bugs and security issues, making it essential to stay updated. For the best experience, ensure your environment runs PHP 7.4 or newer and WordPress 6.7 or newer.
Improvements to UI and Configuration
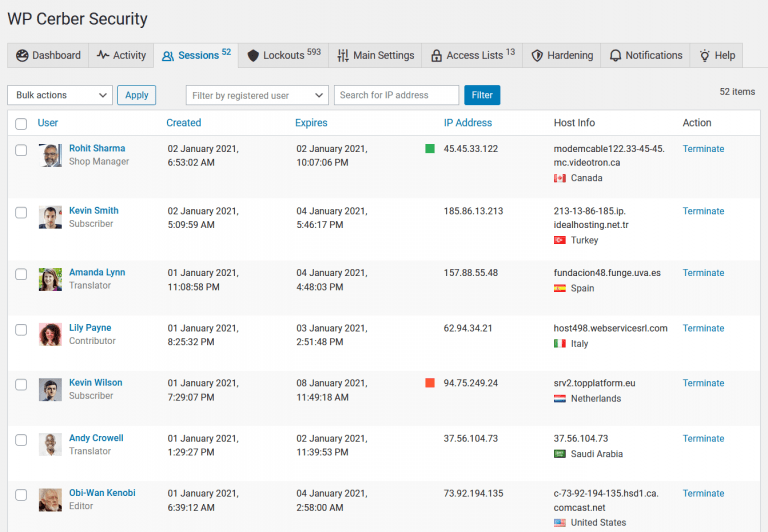
- 2FA Status Display on the Sessions Page
On the Sessions page, users who log in with enforced two-factor authentication are now marked with a green “2FA” label. The label appears as a solid green when the user has successfully entered their 2FA PIN and completed verification. If the 2FA PIN has been sent but verification is still pending, the label is displayed as an outlined green. - Detailed Cookie Information in the Live Traffic Log
Gain a clearer understanding of WP Cerber’s cookies and their behavior. On the “Live Traffic” log, all cookies set by WP Cerber are now highlighted in green within the “Server Response Cookies” section. Additionally, their values are displayed properly decoded for better readability and analysis. - Simplified REGEX Patterns for URL Exceptions
Configuring URL-based exceptions in anti-spam and firewall settings just got easier. REGEX patterns no longer require escaping slashes with backslashes. Any previously configured patterns will be automatically updated during the upgrade process, with unnecessary backslashes removed seamlessly.
Core Improvements
- Continuous Monitoring of IP Address Detection
WP Cerber now continuously monitors potential issues with IP address detection. If the current configuration or web server settings prevent WP Cerber from detecting IP addresses, it will display a detailed diagnostic message. - New Fallback Option for IP Address Detection
When proxy headers are enabled but do not contain valid IP addresses, WP Cerber falls back to using the standard$_SERVER['REMOTE_ADDR']variable to extract IP addresses. The same fallback method applies if the PHP constantCERBER_IP_KEYis configured but does not provide a valid value in the global$_SERVERvariable. - Improved Database Performance
Database-related operations have been optimized to take advantage of the latest technologies available for PHP applications, improving performance on modern web servers.
Improvements to WP Cerber’s 2FA
- Updated 2FA Email Recipient Formatting
When sending 2FA PIN codes, the recipient’s email address now includes their first and last name, instead of just the raw email address. This adjustment aims to improve email deliverability. - Improved Security of 2FA Session Data
The method for storing 2FA session data has been updated to prevent its use as an attack vector if the WordPress database is compromised. This change mitigates the risk of privilege escalation attacks. - Better Handling of 2FA Login Forms
WP Cerber now processes 2FA login forms more effectively on websites where WordPress is installed in a sub-folder, especially in environments with sub-optimal web server configurations.
Wonder what WP Cerber got in the previous version?
Review the release note for WP Cerber Security 9.6.3.
How to update WP Cerber
We recommend enabling automatic updates to ensure you always have the latest security features and performance improvements: how to enable automatic updates in the plugin settings.
How to install WP Cerber
New to WP Cerber? Follow this step-by-step guide to install WP Cerber on your WordPress.
Have any questions?
If you have a question regarding WordPress security or WP Cerber, ask it in the comments below or find answers on the community forum.
Spotted a bug or glitch?
We’d love to fix it! Share your bug discoveries with us here: Bug Report.