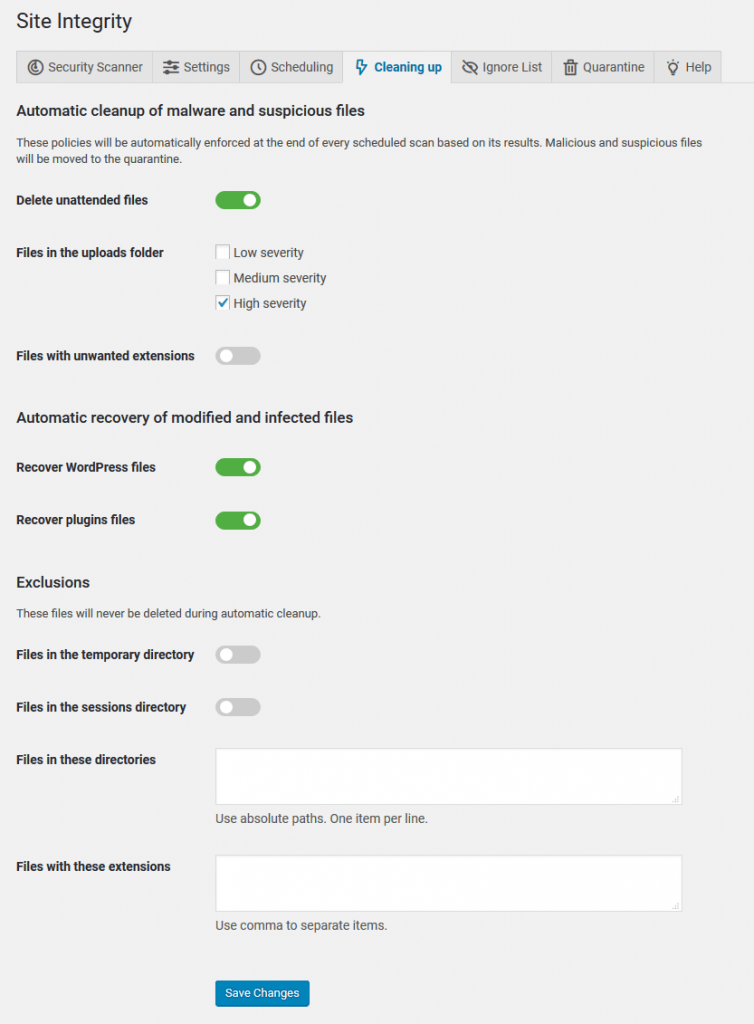
Automatic cleanup of malware and suspicious files
This powerful feature automatically deletes trojans, viruses, backdoors, and other malware and recover infected files. Cerber Security Professional scans the website on an hourly basis and removes malware immediately, providing the best in class threat protection.
Automatic cleanup of malware
If the malware scanner detects malicious files during a scheduled scan, it automatically deletes files moving them to the quarantine. By default this feature is disabled. It’s advised to enable it as shown below.
Automatic file recovery
If the malware scanner detects changes in the WordPress files and plugins, it automatically recovers them. As with the automatic deletion of malicious files, the scanner stores a copy of the recovered file in the quarantine and shows them in an email report.
These automatic removal policies will be enforced at the end of every scheduled scan based on its results. The list of files to be deleted depends on the scanner settings. Please note the following:
- WP Cerber deletes only files that have malicious or suspicious code payload.
- All detected malicious and suspicious files are moved to the Quarantine.
How to restore automatically deleted files
To restore one or more files from within the WordPress dashboard, go to the Quarantine admin page. It’s located under the Site Integrity menu item. Find the filename in the File column and click Restore in the Action column. The file will be restored to its original location.
To restore a file manually, you need to use any file manager in your hosting control panel. All deleted files are stored in a special quarantine folder. The location of the folder is shown on the Tools / Diagnostic admin page. The original name and location of a deleted file are saved in a .restore file. It’s a text file. Open it in a browser or a file viewer, find the filename you need to restore in a list of deleted files and copy the file back to its location by using the original name and location of the file.
Is it possible that scanner deletes vital files by chance?
No. It’s restricted by design. The scanner has comprehensive algorithms to recognize if a file is a part of WordPress, a plugin or a theme. There is only one exception if another plugin or a theme use the uploads folder to store some of its executable code files. Typically those files do not contain malicious code but the scanner shows them as Low severity issues because that is not normal to have executable code files there. Why? The WordPress uploads folder is intended to be used for storing media files like pictures, videos, documents, etc.
To let you safely use such kind of plugins there are three levels of severity you can set for cleaning up the uploads folder. If a file marked as High severity issue, it means it contains malicious code and must be deleted. If you don’t use such kind of plugins, you should enable all three options for deleting files in the uploads folders.
If malicious files have been detected and deleted, the list of deleted files will be shown in every email report.
Know more about the malware scanner
How to use Cerber Security Scanner for WordPress
What Cerber Security Scanner scans and detects
Automated recurring scans and email reporting for WordPress
Cerber Security Scanner Settings explained
Troubleshooting malware scanner issues
Have any questions?
If you have a question regarding WordPress security or WP Cerber, ask it in the comments below or find answers on the community forum.
Spotted a bug or glitch?
We’d love to fix it! Share your bug discoveries with us here: Bug Report.