I’m getting “Probing for vulnerable code”
During its normal operations, the WP Cerber’s firewall inspects all incoming requests to your website and blocks suspicious and harmful ones. It’s normal to see requests marked as “Probing for vulnerable code”. Nowadays they occur regularly and mean the firewall recognized a request as malicious and denied it. You can see them when bots and cybercriminals scan your website for breaches and vulnerabilities in plugins and themes.
On rare occasions, the firewall might erroneously block legitimate requests. If you encounter a problem getting multiple events “Probing for vulnerable code” with a particular URL and this behavior affects some website functionality, this article helps you to solve this issue quickly.
Usually, you might come across this situation if you use a WordPress plugin with flawed code, or if your active WordPress theme adds malformed links to the public pages of your website. On a rare occasion, this can happen if your website has been moved from a set of old PHP pages to WordPress, and you have redirect rules that redirect visitors and search engines to new web pages on your new website.
There are two easy ways to solve this issue
- You can permit requests to a specific URL to bypass Traffic Inspector security rules.
- You can permit requests from whitelisted IP addresses to bypass Traffic Inspector security rules.
Note: you don’t need to do anything if those blocked requests are generated by Googlebot or other crawlers and indexing bots because those lockouts do not prevent search engines from crawling and indexing normal website pages.
How to exclude requests from inspection by specifying an URL
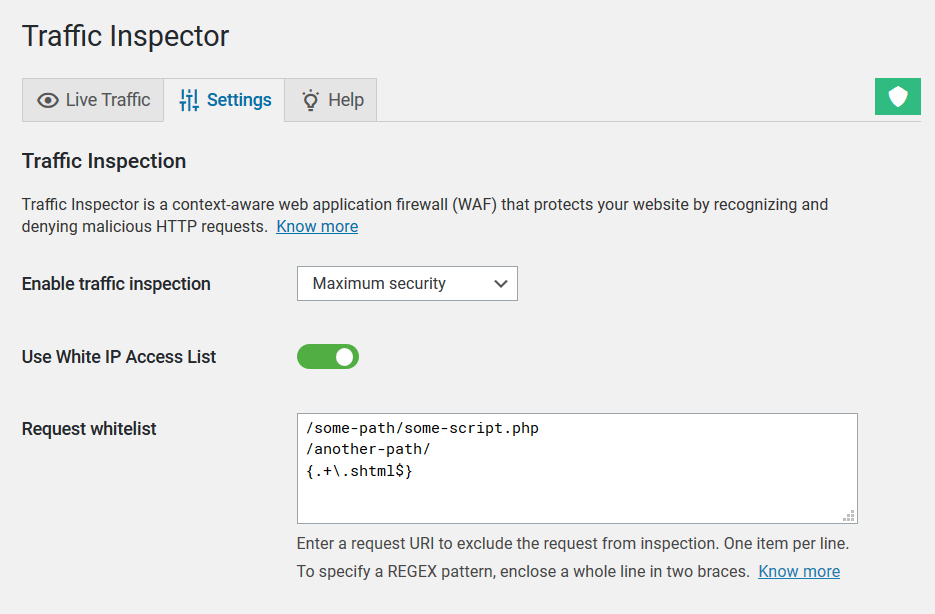
To exclude requests to a specific URL on your website from inspection, use the Request whitelist setting field that is located on the Traffic Inspector Settings admin page.
In this field, you need to enter a request string without the website domain and query string parameters (GET parameters). In other words, you need to take a piece of the URL that starts right after the website domain name and ends on a question mark if it’s present. You can specify as many exceptions (one per line) as you need.
Take a look at this example. For instance, you need to exclude from inspection all requests with a legitimate URL like this: https://wpcerber.com/some-path/some-script.php?something=123. In this case, you need to add the following string: /some-path/some-script.php to the Request whitelist field.
Request whitelist supports regular expressions (REGEX). To specify a REGEX pattern, enclose it in two { } braces. Specify each pattern on a separate line.
For instance to exclude all requests to all pages with the .shtml extension, enter this string: {.+\.shtml$}. To exclude all requests to old website pages with the .php extension, enter this string: {.+\.php$}
A note about escaping: if you use the slash character / in your regular expression, you have to escape it with the backslash \ this way: \/
How to exclude requests from inspection by whitelisting an IP address
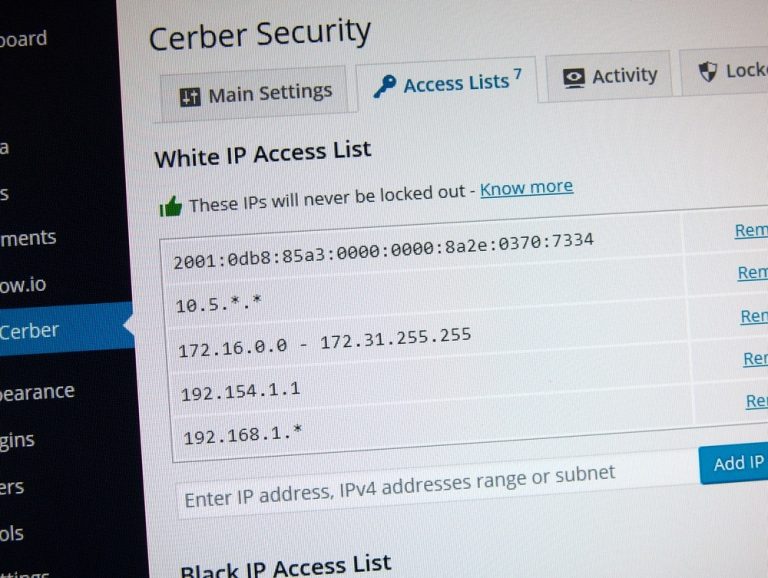
Instead of whitelisting a specific URL, you can permit and exclude from inspection all requests from a specific IP address or a network. You can do this in two simple steps:
- Add an IP address or a network you trust to the White IP Access List
- Go to the Traffic Inspector Settings page and enable Use White IP Access List
Why you see “Probing for vulnerable code”
A request has been inspected and identified as harmful for WordPress by Cerber’s web application firewall (WAF) called Traffic Inspector.
What’s the WP Cerber Security, anyway? It’s a complete and always improving security solution for WordPress which is evolved from a simple yet effective limit login attempts plugin.
Have any questions?
If you have a question regarding WordPress security or WP Cerber, ask it in the comments below or find answers on the community forum.
Spotted a bug or glitch?
We’d love to fix it! Share your bug discoveries with us here: Bug Report.